Free Decryption Tool
• • • • • • • • • • • • Get Permission • Limited-time offer for Cerber 2 victims: Recover your forcibly files without resorting to to attackers to obtain a decryption program. See Also: Check Point Software Technologies has released a free that it says victims can download and use to restore forcibly encrypted ransomware files, including files encrypted by Cerber version 2, which debuted July 29. 'The tool analyzes the sample file the user uploads and generates a private decryption key for the user, which they can then unlock other files with,' a Check Point spokesman tells Information Security Media Group.
Cerber, which in March, is notable for often containing an audio file with a ransom message. The ransomware largely spreads via, security experts say.
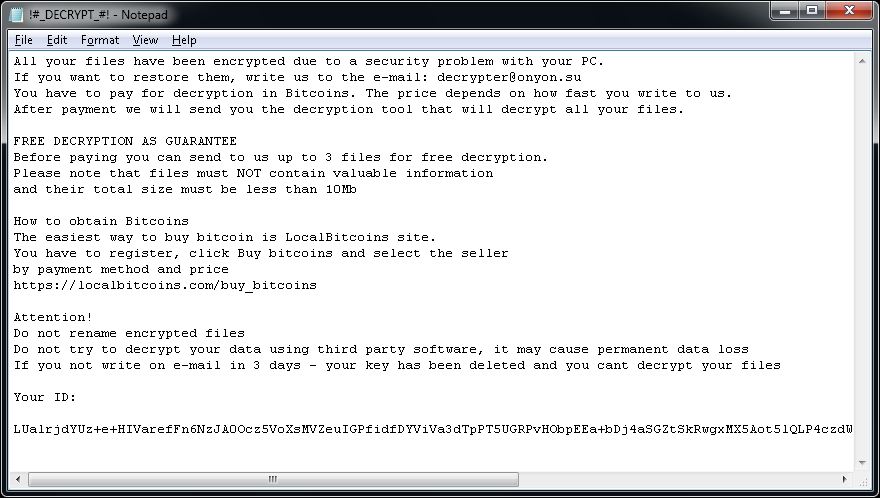
Cerber 2, according to anti-ransomware forum Bleeping Computer, encrypts 455 files extensions, ranging from.backupdb,.doc and.html, to.mp3,.pptx and.zip. Many current versions of Cerber demand a ransom payment of 1 bitcoin, currently worth about $570, according to security researchers. Cerber campaigns are also backed by a customer service team designed to field customer queries, in an attempt to maximize attackers' illicit profits (see ). Azure Case Studies Microsoft Outlook. The ransom notice displayed by Cerber 2.
Source: Bleeping Computer Don't, however, expect the new decryption tool to work indefinitely. Indeed, Cerber 2 appeared to be developers' reaction to a free decryptor released by security firm Trend Micro, which could decrypt some - although not all - Cerber-encrypted files. 'We can decrypt the data because of the weak key that Cerber used,' the developer of Trend Micro's decryption tool, an employee known as, said in a discussion on a Bleeping Computer forum. He added that the weakness could only be used in some cases, suggesting that the average victim might only be able to decrypt about 70 percent of encrypted files using the tool. But Cerber 2 fixes the weakness that Trend Micro was able to exploit, said Aug. 2 via Twitter.

'The author must have read my code,' Panicall said. Check Point didn't immediately respond to a request for comment about whether it planned to participate in the No More Ransom portal, a public-private partnership designed to give ransomware victims a one-stop shop for decrypting their data, if and when related tools are available (see ). New variant of Cerber ransomware confirmed today, not supported by our tool now. The author must have read my code. — panicall (@fuzzerDOTcn) Best Strategy: Avoid Infection The cat-and-mouse game between Cerber's developer and security firms - working on behalf of victims - is a reminder that the best way to deal with a ransomware infection is to never get infected in the first place. For any individual or organization that does suffer a ransomware infection, however, the next step involves mitigation, and deciding on a course of action: Pay the ransom, kiss the data goodbye or decrypt the data using a freely available tool.
Decisions can be complicated by time-related factors. 'Institutions that have time-sensitive records, like hospitals and banks that need to get access immediately, are increasingly being the targets for ransomware,' says Mark Rasch, security evangelist at Verizon Enterprise Solutions (see ). That's because cleaning up from a ransomware infection takes time. Any organization that can't afford to spare that time - not just hospitals and banks but also law firms and any organization involved in sensitive merger-and-acquisition discussions - will face incentives to pay attackers. Affiliate Program The rise of ransomware has been aided by automated attack tools, such as Cerber, that are designed to be used by those who are not technically proficient. In fact, Cerber gets distributed via an affiliate program, Check Point says in a.
Check Point notes that it first found a Russian-language advertisement soliciting new affiliates posted by an individual using the handle 'crbr' on an underground forum in February. 'The ad includes an extensive and accurate explanation about the malware itself, the landing pages, the partnership program through which the malware is sold and the estimated profit,' the Check Point report says.
Based on its researchers' subsequent, presumably anonymous, interactions with crbr, Check Point says that crbr's job is to recruit new affiliates to infect PCs with Cerber. 'In return, the participating affiliate receives part of the profit,' it says. 'In the ad's example, the participating affiliate earns 60 percent of the profits with an additional 5 percent for recruiting a new member to the program. The rest of the money goes to the developer.' The control panel offered to affiliates is available in 12 languages, including Arabic, Chinese, Portuguese and Turkish, crbr told Check Point researchers. According to figures supplied by crbr, 3 percent of all victims - largely hailing from Australia, Canada, France, Germany, Great Britain, India, Italy, South Korea and the United States - pay to purchase the decoder. Cerber Gang: Russians Suspected By tracing communications between Cerber ransomware infections and the dedicated servers used by the developer to manage the infections, Check Point estimates that Cerber ransom payments in July amounted to $195,000 via 161 active campaigns that infected nearly 150,000 victims.
Search for Ransomware Decryptors. Just type in the file extension of your locked/encrypted files and we'll check to see if there's a free decryption tool you can use. Note: Some extensions are used by multiple ransomware variants. Next time block ransomware before it encrypts.
Accordingly, the developer's monthly takings would have been about $78,000, while affiliates would have split the rest. If those takings remain constant, Cerber's developer stands to earn about $1 million per year. 'We believe Cerber originates in Russia, as some of the advertisements appeared in Russian,' Check Point's report says. 'In addition, Cerber's configuration file reveals that the ransomware does not infect targets in the following countries: Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine and Uzbekistan. Typical for Russian malware, this approach allows actors to avoid legal consequences by law enforcement agencies in these countries.' According to a portion of the Cerber 2 configuration file extracted by Trend Micro's Panicall, the ransomware also won't run if it detect anti-virus software from one of 17 vendors, including Avast, Bitdefender, ESET, F-Secure, Kaspersky Lab and Lavasoft.
Check Point says many Cerber infections get spread via exploit kits, noting that victims account for 11 percent of all Cerber ransom payments, while victims account for 8 percent. Schwartz is an award-winning journalist with two decades of experience in magazines, newspapers and electronic media. He has covered the information security and privacy sector throughout his career. Before joining Information Security Media Group in 2014, where he now serves as the Executive Editor, DataBreachToday and for European news coverage, Schwartz was the information security beat reporter for InformationWeek and a frequent contributor to DarkReading, amongst other publications.
He lives in Scotland. From heightened risks to increased regulations, senior leaders at all levels are pressured to improve their organizations' risk management capabilities. But no one is showing them how - until now. Learn the fundamentals of developing a risk management program from the man who wrote the book on the topic: Ron Ross, computer scientist for the National Institute of Standards and Technology.
In an exclusive presentation, Ross, lead author of NIST Special Publication 800-37 - the bible of risk assessment and management - will share his unique insights on how to: • Understand the current cyber threats to all public and private sector organizations; • Develop a multi-tiered risk management approach built upon governance, processes and information systems; • Implement NIST's risk management framework, from defining risks to selecting, implementing and monitoring information security controls.
This guide provides the instructions and location for downloading and using the latest Trend Micro Ransomware File Decryptor tool to attempt to decrypt files encrypted by certain ransomware families. As an important reminder, the best protection against ransomware is preventing it from ever reaching your system. While Trend Micro is constantly working to update our tools, ransomware writers are also constantly changing their methods and tactics, which can make previous versions of tools such as this one obsolete over time. Customers are strongly encouraged to continue practicing safe security habits: • Make sure you have regular offline or cloud backups of your most important and critical data. • Ensure that you are always applying the latest critical updates and patches to your system OS and other key software (e.g. • Install the latest versions of and apply best practice configurations of security solutions such as Trend Micro to provide mutli-layered security. Trend Micro customers are encouraged to visit the following sites for more information on ransomware and prevention best practices: Consumer (Home) customers may visit the following site: Corporate (Business) customers may find additional information and guides here.
* - CryptXXX V3 decryption may not recover the entire file (partial data decryption). Please see the section titled Important Note about Decrypting CryptXXX V3 below.
** - Users will need to contact Trend Micro technical Support to request the separate tool TeslacryptDecryptor 1.0.xxxx MUI for TeslaCrypt V1 and V2 files. Both tools support V3 and V4. Obtaining and Executing the Tool(s) • Click the Download button below to obtain the latest version of the Trend Micro Ransomware File Decryptor tool. Decompress (unzip) and then launch the included RansomwareFileDecryptor exe file. • Upon launch, users will be required to accept the End User License Agreement (EULA) to proceed. • After accepting the EULA, the tool will proceed to the main user interface (UI). From here, users will be presented with a step-by-step guide to perform the file decryption.
Due to the advanced encryption of this particular Crypto-Ransomware, only partial data decryption is currently possible on files affected by CryptXXX V3. The tool will try and fix certain file formats after the decryption attempt, including DOC, DOCX, XLS, XLSX, PPT, and PPTX (common Microsoft Office) files. The fixed file will have the same name of the original file with '_fixed' appended to the file name and will be placed in the same location. When opening the fixed file with Microsoft Office, it may present a message to try and repair the file again, and this process may be able to recover the document. Please note that due to the different versions of Microsoft Office and particular file behaviors, it is not guaranteed that this method will completely recover the document.
However, for other files after the partial data decryption, users may have to utilize a 3rd party corrupted file recovery tool (such as the open source program JPEGSnoop*) to try and recover the full file. An example of this would be a photo or image file that is partially recovered to show parts of the image, but not the entire image. A user would then determine if the file is critical enough to utilize a 3rd party tool or seek assistance from an 3rd party professional file recovery service. Original Photo (before CryptXXX V3 infection) Photo after partial data decryption Unfortunately, Trend Micro Technical Support will be extremely limited in any sort assistance that can be provided regarding 3rd party file recovery.
BadBlock can encypt essential system files, which may cause issues like not allowing the operating system (OS) to load properly after a reboot if infected. Because of the sensitivity of these files, when the tool attempts decryption of these files, it will backup selected key originally encrypted PE files and append “_bbbak” to the name. After the decryption, the original PE file name will be restored.
For non-PE files, the decrypted names will be the original file name with “_decrypted” appended to the name of the file. Ince there are different ways that BadBlock can affect a system, there are a few different approaches the tool may use to try and decrypt affected files: • If the system has been infected and had not yet had a reboot. In this situation, the user may try and run the tool and it will attempt to decrypt affected files. • If the system has already been rebooted after an infection and cannot boot successfully into the OS.
In this situation it is recommended that the user boot from an OS installation image (such as a Windows Recovery Disk) or other method to try and get to a state where the OS can boot successfully and then try and run the tool to decrypt other files. • If the system OS cannot be recovered by an OS installation image as mentioned above. In this case, users may need to physically remove the affected hard disk drive (HDD) and mount it on another known working system as a extra drive and attempt to run the tool from the other system.
CERBER decryption must be executed on the infected machine itself (as opposed to another machine) since the tool needs to try and locate the first infected file for a critical decryption calculation. Due to the method of decryption for CERBER, the tool may take several hours (average is 4) to complete decryption on a standard Intel i5 dual-core machine. In addition, the encryption logic for CERBER also is built in such a way that the more cores a CPU has, the lower percentage chance of success for the decryption because of its complexity. Similar to some other types of ransomware encryption, some files may be only partially decrypted and may require a subsequent file repair.
Because this tool uses brute-force to calculate keys for Globe/Purge, decryption could take more than twenty (20) hours. The average decryption time varies from approximately ten (10) hours with a 4-core CPU machine to thirty (30) hours with a single-core PC machine. To decrypt Globe/Purge V1, the decryption process must be run on the originally infected machine. Please note that the tool cannot decrypt files on a FAT32 system due to a bug in the ransomware itself.
This is also a limitation of the ransomware author's original decryption tool. This tool searches for a private key in the ransomware process memory - which means it is only effective if the original WannaCry ransomware process still exists and is actively running.
If the infected machine is rebooted, the ransomware process is somehow stopped after the initial infection, or any other situation occurs that would affect the process memory of the infection machine the decryption will fail. It is very important that users do not try and reboot their system before trying the tool. It is currently unknown how long the prime numbers (related to the private key) will be stored in the memory address space before being reused or overwritten. Therefore it is highly advantageous to run this tool early in the infection chain rather than later.
Based on internal Trend Micro testing, this tool has the highest success rate on Windows XP (x86) machines compared to a very low rate on other versions of Windows - but individual users' success rate will vary.